Continuous detection and takedown of scams
A software-mediated enforcement system that identifies and removes impersonation, phishing, malicious apps, and illegal gambling scams across multiple channels. The same system underlies Eydle’s product-level security verification.
How it works

Detection
Eydle continuously monitors for product impersonation across web, social platforms, advertising channels, and app stores. The system applies visual and behavioral analysis to identify scams targeting your product and customers.

Structured Verification
Detected scams are examined through a defined verification workflow. Automated analysis performs repeatable checks, with human judgment applied at defined escalation points to ensure accuracy and defensibility.

Coordinated Takedowns
Verified scams are routed through established reporting and removal channels. The system tracks actions and outcomes to maintain consistency and documentation across takedown efforts.
Teams have structured visibility into detected and verified scams, with alerts and integrations available as needed.
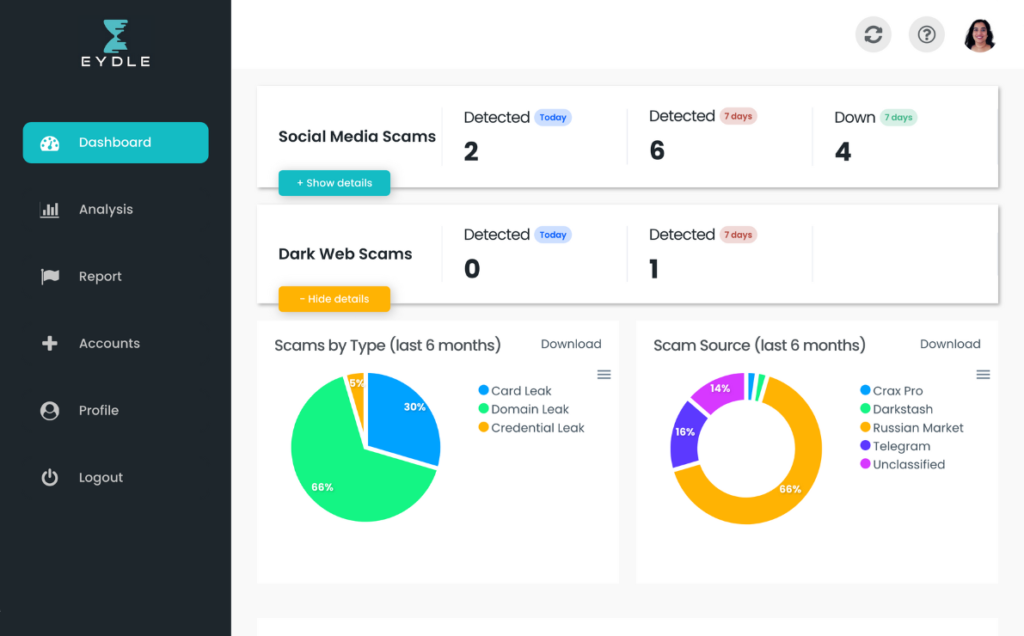
Measurable enforcement impact
Continuous detection and structured takedown reduce active scams before they scale. Removing scams early limits customer harm, operational burden, and reputational risk.
80% reduction in active scams
Customers typically reduce active scams by 80% within the first three months of continuous enforcement.
Higher detection accuracy
Visual and behavioral analysis identifies more scams than keyword-only monitoring while maintaining low false positives.
Enforcement coverage
Eydle enforces against product impersonation and abuse across social platforms, web domains, mobile app stores, advertising platforms, and online marketplaces. The system identifies and verifies active scams targeting your product and customers.
Illegal Gambling Scams
Identify phone numbers, bank accounts, and QRIS codes used to receive illegal gambling payments.
Phishing and Cloned Websites
Detect and take down phishing domains and cloned landing pages designed to mislead users.
Malicious Mobile Applications
Identify and remove unauthorized or malicious applications distributed through app stores.
Impersonation on Social Media
Identify and remove fraudulent profiles and accounts impersonating your product or brand.
