Previously we discussed pig butchering mobile scam apps that impersonated popular investment firms such as Sequoia. Although this allowed the apps to ensnare victims, they were more susceptible to being detected and taken down. In this article, we discuss pig butchering scam apps that hide their malicious intent by using vague mobile app store listings.
The listing in the mobile app store does not directly disclose the trading functionality of the app. When a user installs and runs the app, they see the malicious trading functionality. This tactic makes it harder to detect the scam.
To ensnare victims, scammers share links to these mobile apps via Facebook pages and Whatsapp groups. In the last three months, we observed hundreds of such apps listed on Google Play Store and Apple App Store.
To recall, a pig butchering scam is a type of financial scam where the victim is gradually “fattened up” (like a pig) with promises of high returns on investments, only for the scammer to “slaughter” the victim by taking all their money in the end. Generally, these apps allow users to trade in stocks and related assets, with the primary method of payment being crypto and virtual currencies that are hard to trace and recover.
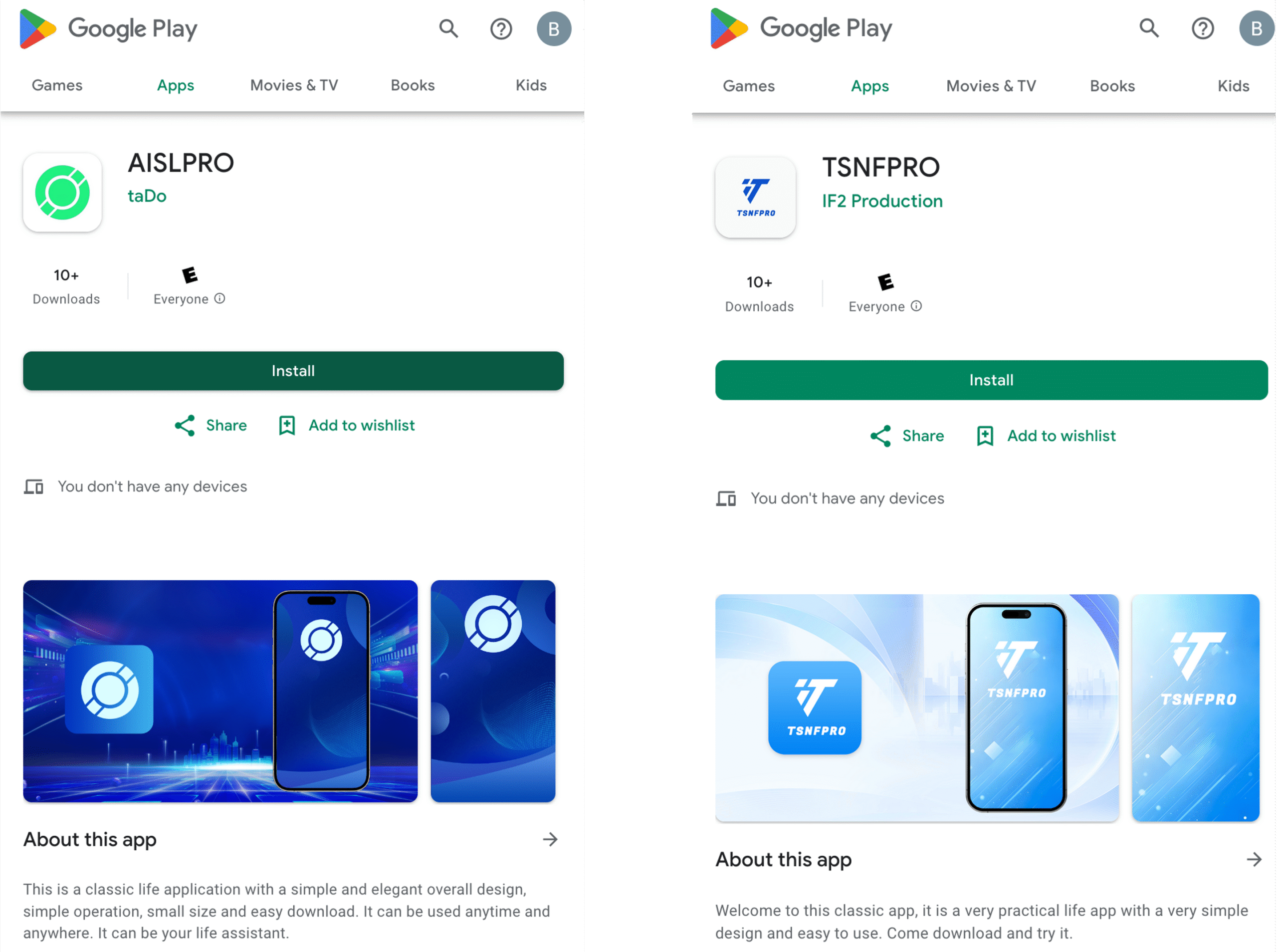
The description for AISLPRO states, “This is a classic life application with a simple and elegant overall design, simple operation, small size and easy download. It can be used anytime and anywhere. It can be your life assistant.” This is very vague and does not disclose the core trading functionality of the app. The description for TSNFPRO is similarly vague.
Both apps list their category as “Finance.” However, other apps choose categories such as “Business” or “Tools.” This makes the app listing even more vague and easier to hide their malicious intent.
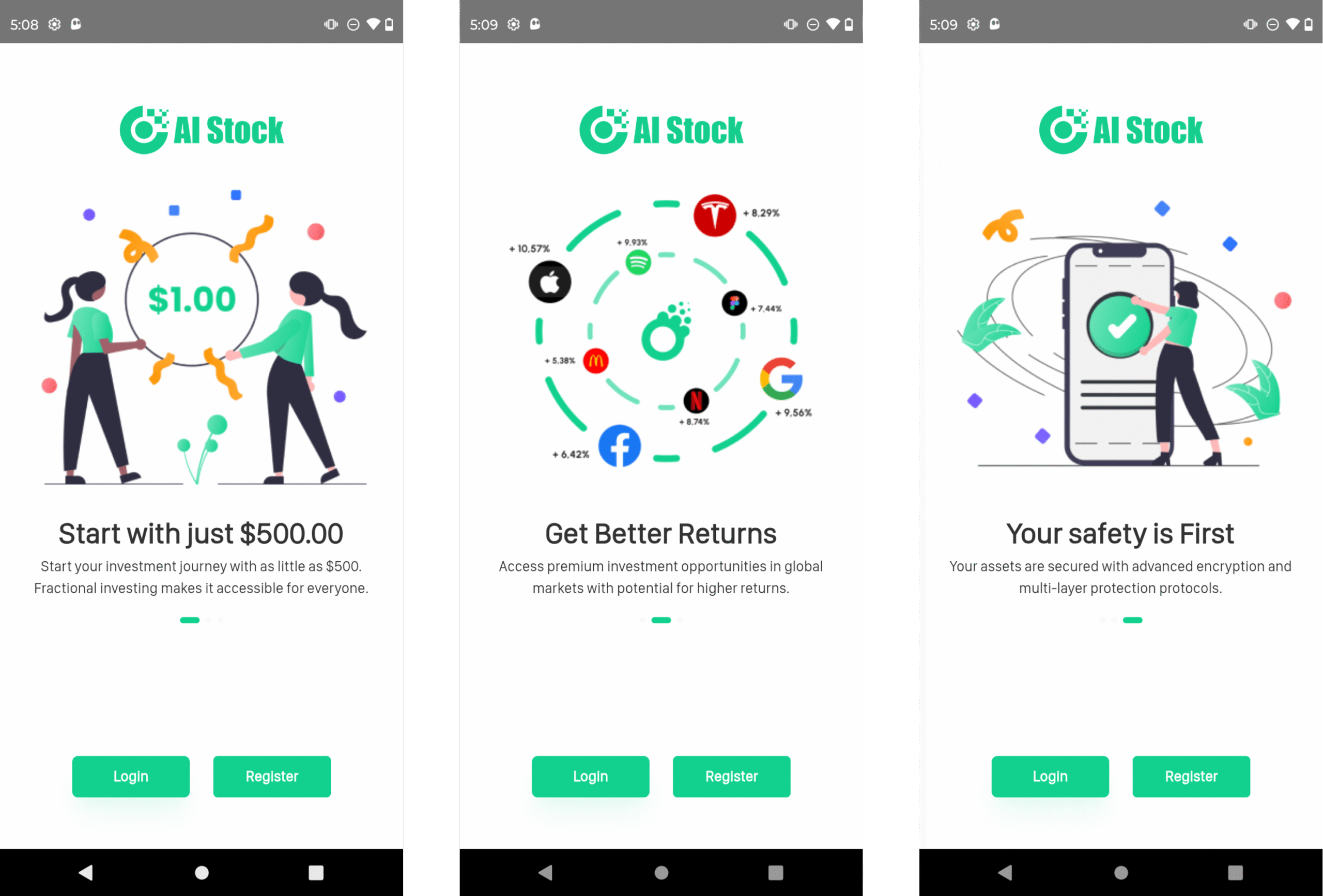
When a user installs the AISLPRO app, the user sees the actual trading functionality. Figure 2 shows screenshots of the running app mentioning the “AI Stock” and investment amounts. The app redirects the user to a malicious website: https://app.stockoi[.]com/#/welcome. Although Google has taken down the AISLPRO app, the malicious website is live as of July 16, 2025.
About Eydle
The Eydle Scam Protection platform helps enterprises proactively identify and take down scams that target customers and employees. To learn more, visit our website. For questions regarding the blog post, email [email protected].




