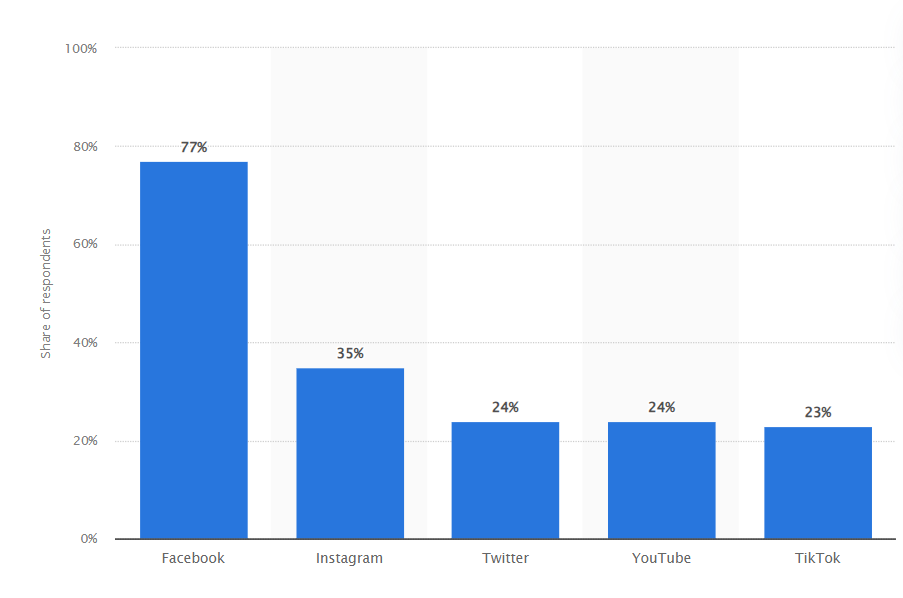
Social media has largely influenced how people communicate, form connections, and conduct business in today’s world. These platforms are now an essential part of daily life, with an astounding 4.9 billion users worldwide in 2023. With a market value projected to reach $49.09 billion in 2022, social media’s influence goes beyond just interpersonal communication as companies use it to engage with clients [1].
However, as social media’s popularity rises, scammers have capitalized on this trend, attempting to target and compromise social media accounts for personal gain.
Common social media hacking techniques
To hack social media accounts, scammers use a variety of techniques, including:
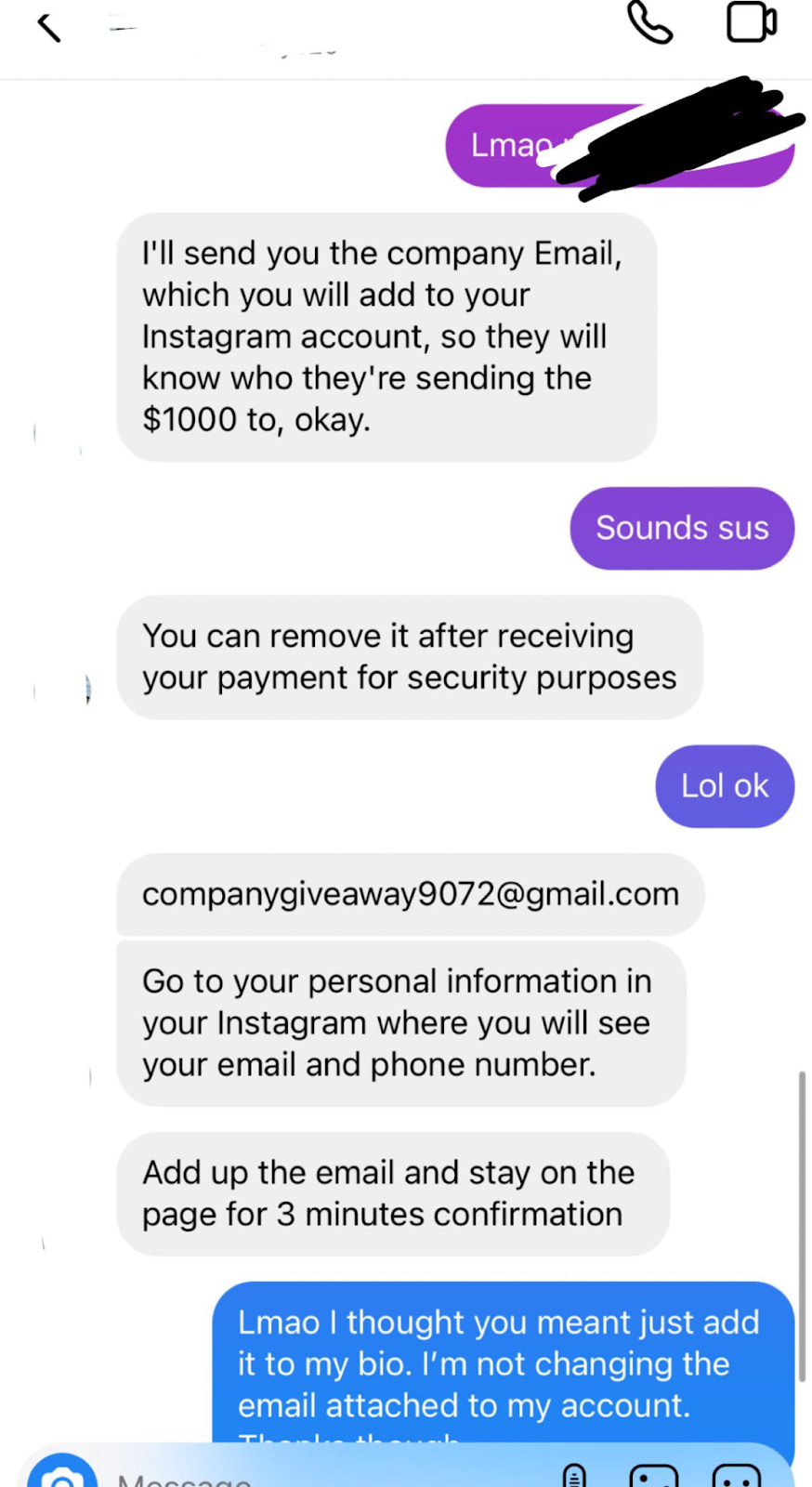
1. Phishing Attacks: Scammers trick users into divulging their login information or clicking dangerous links by sending phony emails or messages that appear to be from reliable sources.
2. Data breach: Attackers may directly target the social media company’s systems to obtain a database of user credentials or private information.
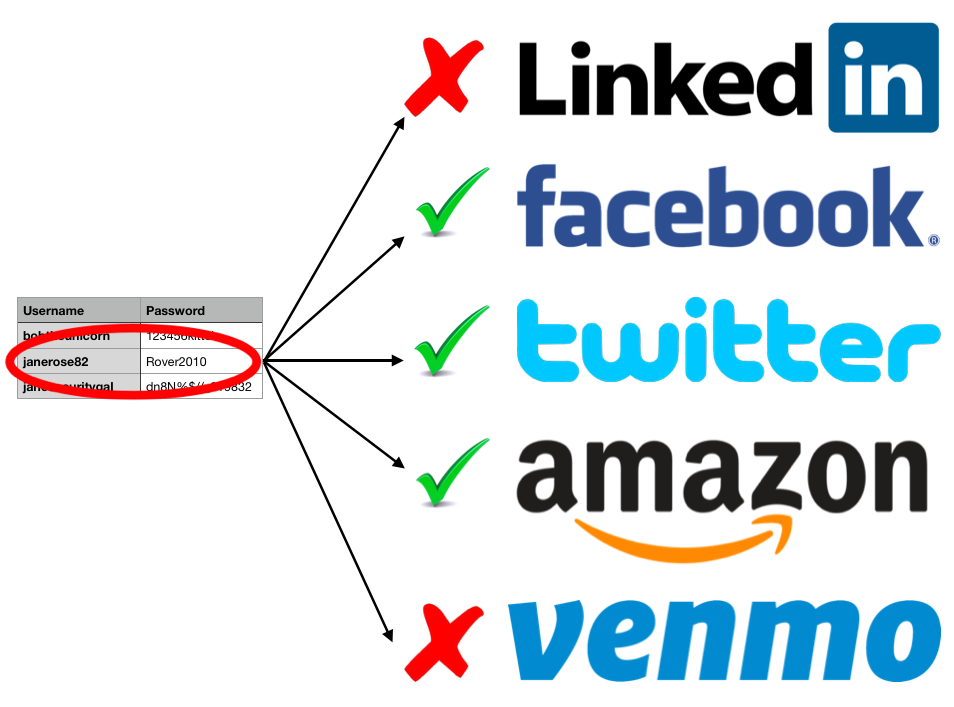
3. Credential stuffing: Hackers attempt to log into social media accounts where users have reused the same login credentials by using usernames and passwords from previous breaches.
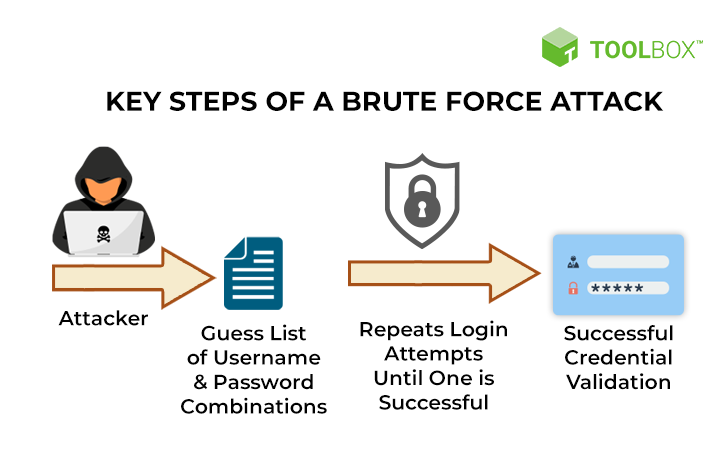
4. Brute Force Attacks: Attackers use automated tools to guess passwords by attempting several different combinations until they find the one that works.
5. Spyware is a type of harmful software that invades a user’s computer, steals data from it, and then shares it with third parties without their consent.
6. Fake Apps and Extensions: Malicious actors create counterfeit social media apps or browser extensions that claim to offer additional features but, in reality, steal login credentials or access tokens when users log in.
Why do scammers break into those accounts?
Multiple factors lead hackers to target social media accounts:
1. Personal Information: Social media profiles frequently include personal information like names, birthdates, and addresses. Hackers may use this data for targeted phishing attacks, social engineering schemes, or identity theft.
2. Financial Gain: Social media accounts can give hackers access to sensitive payment information or linked financial accounts, which they can use to their financial advantage. Also, they can demand a ransom from the account owner in exchange for returning control.
3. Impersonation: Hackers may use compromised accounts to pass themselves off as real people to deceive others, harm their reputations, or run scams.
4. Political and Social Manipulation: By taking over powerful accounts, hackers can sway public opinion, disseminate misinformation, or obstruct crucial discussions. You can read more about a real-world example of taking over influential accounts on Twitter in this article.
5. Harassment: Hackers might be motivated by personal hard feelings, harassment, or a desire to humiliate the account owner.
How to protect yourself against hacking
There are some crucial actions to take to protect your online safety and secure your social media accounts:
- Setting up strong, unique passwords for all of your online accounts is your first line of defense. These passwords should contain a variety of uppercase and lowercase letters, numbers, special characters, and other characters to make them secure and unique for each account. Do not use common words or dates that are easy to guess, like birthdays.
- Turn on two-factor authentication (2FA) that requires a second verification step in addition to your password, such as a one-time code sent to your mobile device or generated by an authentication app. This significantly lowers the risk of unauthorized access because even if someone knows your password, they still need the secondary code to access your account.
- Be aware of unsolicited DMs, emails, and links that seem shady. Carefully read the message for any indications of phishing, such as misspellings, odd requests, or content that makes you suspicious.
- Update your software frequently, including your operating system, web browser, and security programs, to fix well-known vulnerabilities, making it more difficult for hackers to take advantage of flaws in your system.
- To limit who can see your personal information, review and modify your privacy settings. Accept friend requests or connections with caution, and refrain from disclosing private information to strangers.
If one of your social media accounts has been compromised, start by ensuring that your computer’s security software is updated. Afterward, initiate a scan for potential threats. If the scan detects any suspicious software, remove it and reboot your computer. Next, adhere to the account recovery instructions provided by each platform: Facebook, Instagram, Twitter, Linkedin [7]
Protect your online presence with Eydle
Empower your brand’s defense against online scams and cyber threats today with Eydle. Our advanced AI technology and vigilant human oversight offer a potent shield against impersonation and fraud on social media platforms.
Explore our comprehensive protection services at eydle.com or reach out to us at [email protected]. Your brand’s security is our top priority, and we’re here to assist you every step of the way.
Resources:
1- https://www.forbes.com/advisor/business/social-media-statistics/#source
4- https://www.ckd3.com/blog/credentialstuffing
5- https://www.spiceworks.com/it-security/cyber-risk-management/articles/what-is-brute-force-attack/
6- https://www.imperva.com/learn/application-security/social-engineering-attack/
7-https://consumer.ftc.gov/articles/how-recover-your-hacked-email-or-social-media-account
Protect Your Social Media from Hacking was originally published in Eydle on Medium, where people are continuing the conversation by highlighting and responding to this story.