In recent years, and notably after the pandemic, more people and businesses are going online. Cybercriminals took advantage of this situation and turned it into an opportunity to target users’ computers and networks to steal sensitive information. More than $4.1 billion was lost in the US due to cybercrime in 2020.
Cyberattacks have evolved along with the the online system over the years. For example, as businesses move to large and well-known online platforms such as Google or Facebook to host their websites, phishing, which is a type of cyberattack discussed below, has also moved to those platforms, making it difficult to recognize an attack by simply looking at the URL and the IP address of the website.
In general, the number and complexity of attacks have increased, which has led to an increase in the demand for advanced cybersecurity and cyber protection strategies that can counter those threats.
Artificial Intelligence (AI) is attracting a lot of attention in this regard. Below we briefly summarize the common types of cyberattacks in existence today before discussing how AI is emerging to provide effective tools for cybersecurity.
Common types of cyberattacks
Malware: It is a malicious software intended to harm, disable or exploit any computer device, service, or network. There are different types of malware: virus, ransomware, scareware, worms, spyware, trojans, and adware.
Denial of Service (DoS): This is a cyberattack that aims to slow down or interrupt a service or a network by flooding the target with multiple simultaneous requests which prevent other users from accessing it.
Phishing: It is a cyberattack designed to lure users into giving their personal information, login credentials, and banking data via text messages, telephone calls, and social media DM’s by impersonating a legitimate company or business.
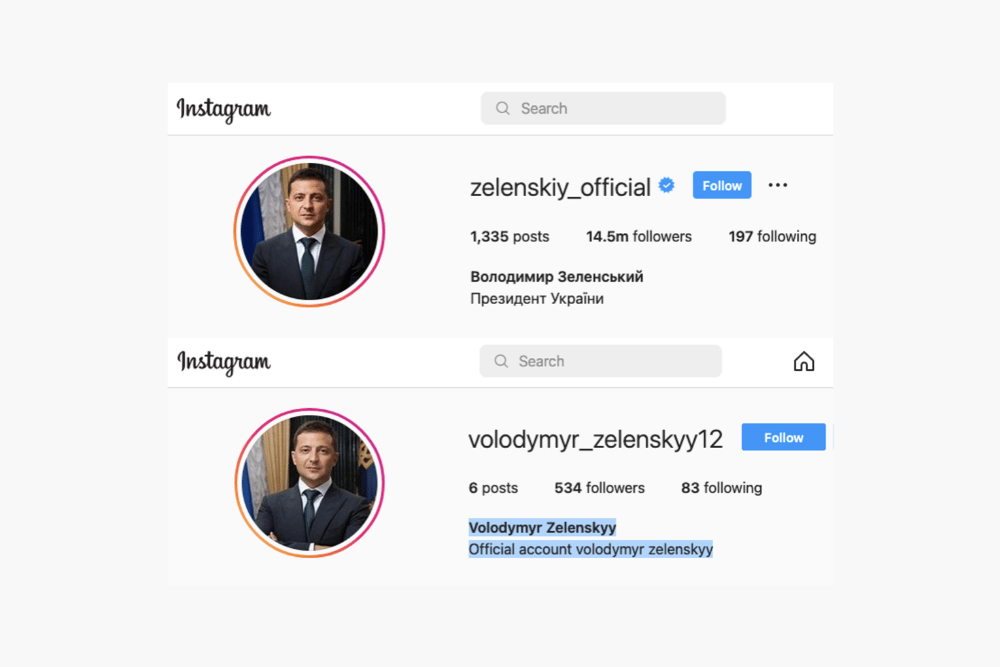
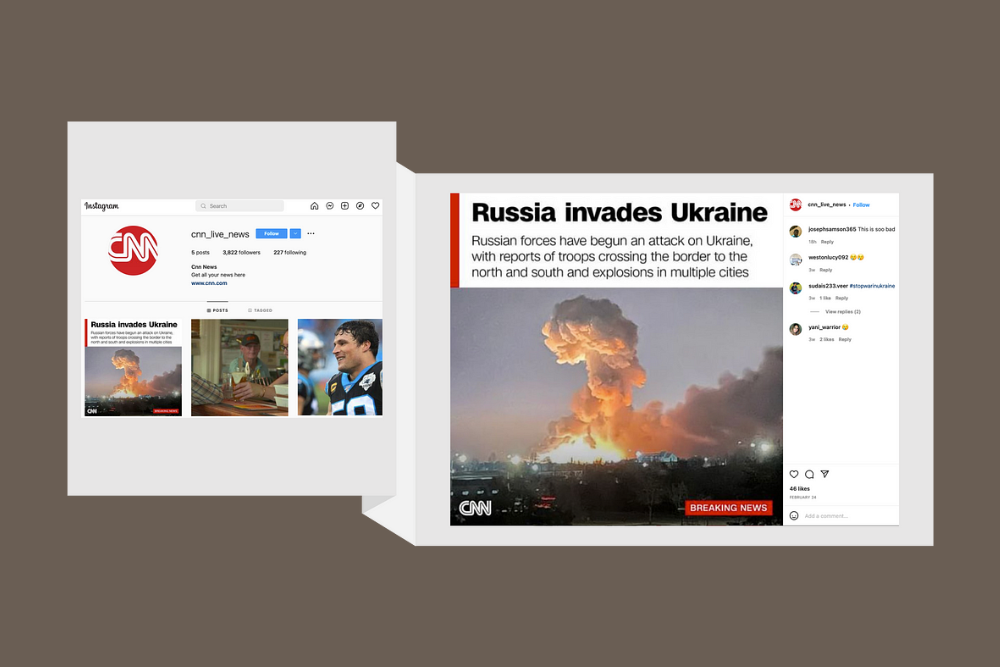
Phishing attackers can send you an email or a message on social media asking you to give some information or to visit a spoofed website that looks identical or very similar to the real one. You can read more in this article “Anatomy of Brand Phishing Attacks on Instagram”.
Zero-day attack: This is a method that takes advantage of security flaws and vulnerabilities in a system that are unknown to the system developer and users. When an attacker spots a vulnerability before the software programmer has fixed it, the attacker can implement a code to victimize the software users by delivering spyware and stealing their identity information.
AI for cybersecurity
These ever-changing attacks demand more sophisticated cybersecurity defenses that can overcome the weaknesses of the existing cyber security methods such as Intrusion Detection Systems or Intrusion Prevention Systems (IDS/IPS).
Machine learning and deep learning methods can understand attack mechanisms and patterns in attacker and user behavior by processing billions of data points effectively. This can accelerate threat detection, reduce duplicative processes and eliminate time-consuming tasks. In fact, depending on the application and the quality of data available, AI can identify unknown threats that humans can not notice or foresee. Due to these advantages, integrating AI technology into the cybersecurity defense system offers a lot of promise.
AI methods applied to cybersecurity
As advances in computing hardware and algorithms become more accessible, Machine Learning (ML) and Deep Learning (DL) techniques can be used to analyze and classify malicious files from a large amount of data to detect a cyber threat.
ML approaches can be divided into supervised learning and unsupervised learning. Two common types of supervised ML tasks are classification and regression.
In classification, the model learns the likelihood of an input data item belonging to one of the possible classes.
In regression, the supervised learning-based model learns the continuous mapping between inputs and outputs such that given a new input, the model can compute the corresponding output.
Unsupervised learning is usually applied to identify patterns or groups in a given dataset.
Deep Learning, which is a subfield of Machine Learning, uses neural networks that are inspired by the human brain. Deep learning has the ability to process large volumes of data to learn underlying correlations between input and output quantities in a cost and time-effective manner to automate perception-related tasks such as image recognition. These AI methods have the potential to be developed into cybersecurity tools that can eliminate the flaws of traditional detection approaches.
Cybersecurity solutions powered by AI
Some companies and research centers have started to include ML and DL methods in their cybersecurity solutions. Examples are as follows:
Malware detection: Global cyber security companies such as Kaspersky detect mobile and computer malware by training ML and DL models on huge datasets of benign and malicious samples.[1]
Denial of Service: Research has been done to detect DoS using Deep learning. In one solution, the detection model was trained on different datasets such as “Darpa” which contains communication data between source and destination IPs.[2]
Zero-day attack: “Check Point Software Technologie” developed a DL model trained on their huge “threat cloud database” to prevent potential attacks and unknown vulnerabilities. [3]
In the research paper entitled “Utilising Deep Learning Techniques for Effective Zero-Day Attack Detection”, the zero-attacks model detection was trained on benign and malicious classes of insider and outsider attacks traffic. This dataset was generated by “the Canadian institute for cybersecurity”[4].
Phishing: The existing phishing methods are trained to detect phishing emails and websites. With the growth of social media phishing attacks, there is an urgent need for detection methods that will prevent this type of cybercrime. For example, a traditional URL analysis or IP reputation-based detection will not catch such attacks because they are hosted on Instagram, Twitter, and LinkedIn which are reputed websites.
How Eydle applies AI to address social media phishing
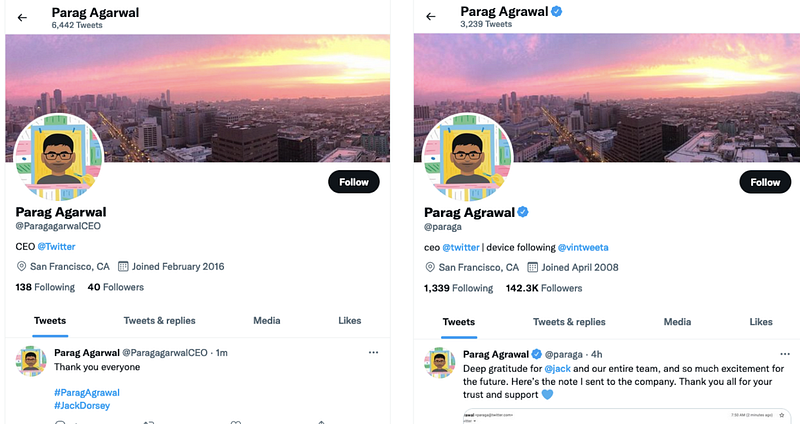
Eydle’s AI-powered platform uses deep learning tools to detect impersonation accounts on social media platforms, such as Instagram, LinkedIn and Twitter. Figure 1 shows an impersonation example of Twitter’s CEO on the Twitter platform.
The impersonation account looks and feels very similar to the real account: the account image has been copied, account names are very similar (except for one alphabet), and the person’s location and designation are similar. The scammer creates such visual similarity between the two accounts and exploits it to deceive people, e.g. followers and employees, into divulging their personal/financial information to the scammer. Damage to the person’s or company’s brand reputation is another type of loss resulting from such impersonation.
Eydle’s platform analyzes these visual elements of the account page to detect phishing and impersonation accounts. The platform uses YOLO-type object detection models and whole page analysis models, based on facial recognition technology, that analyze the layout of different page elements, color, font scheme, images, and text in comments and posts. Combined with a deep learning model for the URL analysis, the platform uses a multi-pronged, automated approach to detect the phishing intention of the page with high accuracy. The approach is backed by the latest research in the emerging field of AI and cybersecurity. You can read some of the details on the object detection model in this article.
Conclusion
With the increase in number and complexity of cyberattacks, companies and individuals should be aware of today’s security issues and concerns, such as social media phishing and impersonation, that could threaten their business and personal data. It is equally important to invest in modern protection solutions that are backed by science and have shown promise in research.
AI-based tools are at the forefront of such solutions. You can learn more about Eydle’s AI-powered brand protection solution at www.eydle.com.
References
[1] “Kaspersky-Lab-Whitepaper-Machine-Learning.pdf.” Accessed: Dec. 01, 2021. [Online]. Available: https://media.kaspersky.com/en/enterprise-security/Kaspersky-Lab-Whitepaper-Machine-Learning.pdf
[2] S. Sumathi and N. Karthikeyan, “Detection of distributed denial of service using deep learning neural network,” J Ambient Intell Human Comput, vol. 12, no. 6, pp. 5943–5953, Jun. 2021, doi: 10.1007/s12652–020–02144–2.
[3] “How to Prevent Zero Day Attacks,” Check Point Software. https://www.checkpoint.com/cyber-hub/threat-prevention/what-is-zero-day-attack/how-to-prevent-zero-day-attacks/ (accessed Dec. 01, 2021).
[4] H. Hindy, R. Atkinson, C. Tachtatzis, J.-N. Colin, E. Bayne, and X. Bellekens, “Utilising Deep Learning Techniques for Effective Zero-Day Attack Detection,” Electronics, vol. 9, no. 10, p. 1684, Oct. 2020, doi: 10.3390/electronics9101684.