Attacks can lead to ID theft and chilling effect on engagement
Brand impersonation on social media is becoming a major problem for businesses worldwide. According to the US Federal Bureau of Investigation, Internet fraud including impersonation and phishing contributed to $4.2 billion losses in 2020.

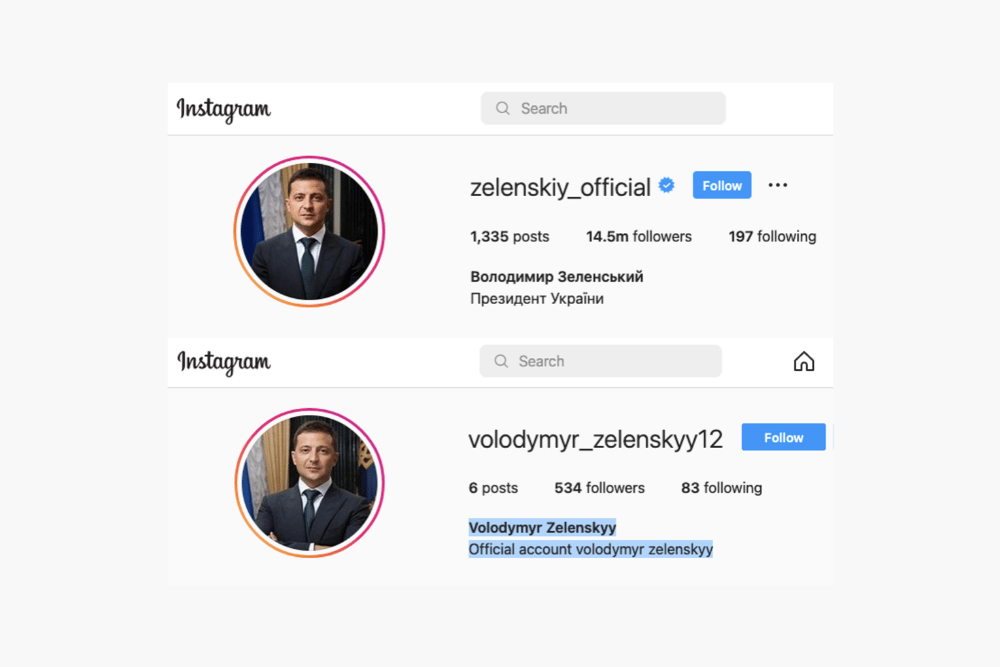
Our previous article explained how attackers create Instagram accounts that impersonate a brand. To impersonate a brand, attackers can (1) create a new account or (2) take over an existing account. In both cases, they make the impersonation account look and feel like the real brand account. Attackers follow similar methodology to impersonate brands on other social media platforms such as Facebook and Twitter.
What happens after attackers create an impersonation account? Do the attackers wait passively for users to fall prey to these accounts? The short answer is, no. In this article, we discuss how attackers weaponize these accounts to actively pursue users and perpetrate fraud such as ID theft, stealing login credentials and donation scams.
Methods to weaponize impersonation accounts
Users who engage with a brand on social media are prime targets for attackers who impersonate that brand. Users who engage with a brand are likely to be existing customers or employees of the brand. Hence, by targeting such users, attackers have a higher chance of succeeding in their fraud campaigns.
Engaging with a brand includes following the brand’s account, liking posts from the brand’s account and commenting on the posts from the brand’s account.
After creating accounts that impersonate a brand, attackers use the following methods to target users who engage with the brand:
- Send direct message (DM) to a user
- Comment on a user’s post
- Start following a user’s account
To explain each method, we use examples related to neobanks such as Chime (810k followers), Current (74.2k followers), Varo (89.4k followers) and Yotta (30k followers). We also use examples related to ID.me (10.6k followers), an identity and authentication provider. The examples are representative of attacks we have observed against hundreds of other brands on Instagram.
Method 1: Direct Messaging the user
When a user engages with a brand, attackers send them direct messages from accounts that impersonate that brand. Consider a user who just started following the brand Varo. Figure 2 shows a direct message sent by an attacker to such a user. The attacker sends the direct message from an impersonation account that has a handle varo_lit and is using Varo’s logo. Because the user started following Varo, the user is less likely to be surprised to receive the message, which looks like it is from Varo.
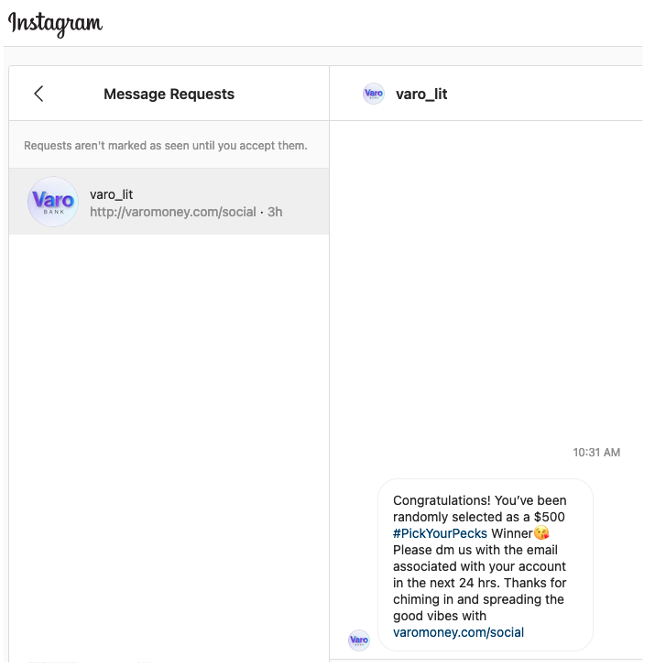
The message congratulates the user on being selected as a winner of $500, and requests the user to provide email and account information via a direct message. To appear legitimate, the attacker has included a link to Varo’s actual website varomoney.com in the message. Attacker has established a communication channel via direct messaging and does not need a website to collect information. Alternatively, attackers can include links to fraudulent phishing websites and redirect users to those websites to collect sensitive information.
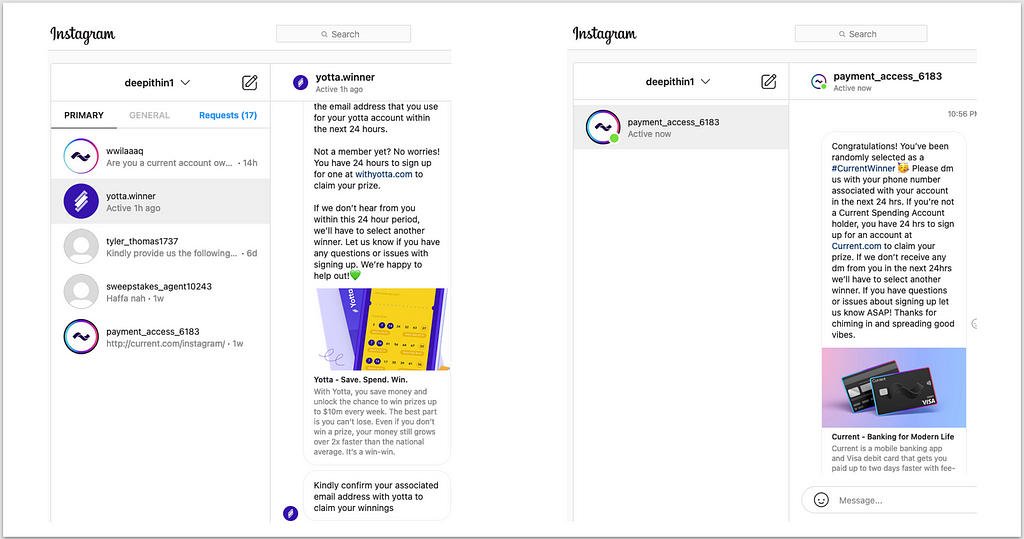
Figure 3 shows two more direct messages sent by attackers. Here they are impersonating the brands Yotta and Current, and are trying to get sign up name, email and phone number. In the Chime example, the user received the direct message within an hour of following the real Chime account.
Method 2: Commenting on user’s post
When a user engages with a brand, attackers can target the user by commenting on the user’s posts. Note that attackers use impersonation accounts to comment on the user’s posts and not on the brand’s post.
Figure 4 shows an Instagram post from the brand Chime. A user who is following Chime’s account, engaged with Chime by liking the post.
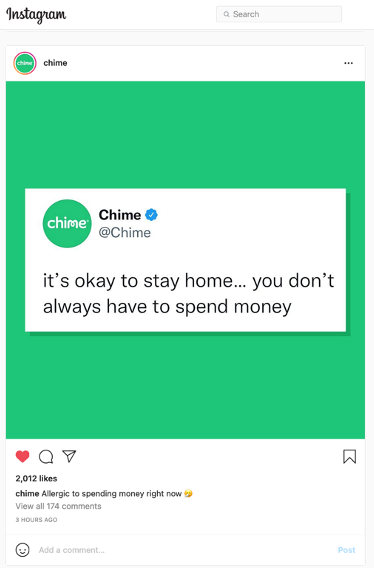
Within a short period after the user liked the post, four accounts impersonating Chime commented on the user’s latest post. Figure 5 shows these four comments.
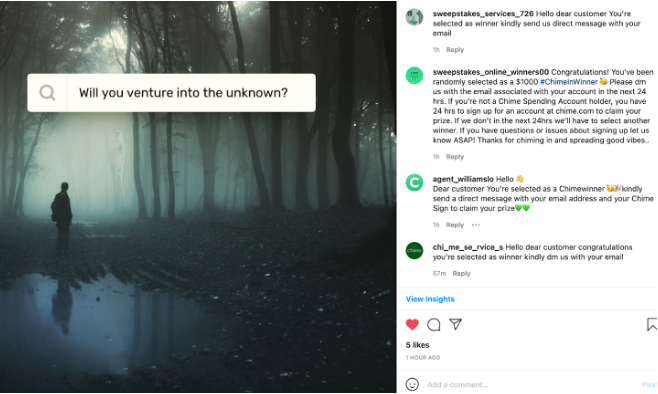
Figure 6 shows comments from attackers impersonating Varo and Current. Attackers are using impersonation accounts whose logo and handle are similar to that of Varo and Current. Many brands do have multiple social media accounts for different products, departments, countries etc. Hence the user might be deceived into believing that the comments are coming from an account belonging to the brand.
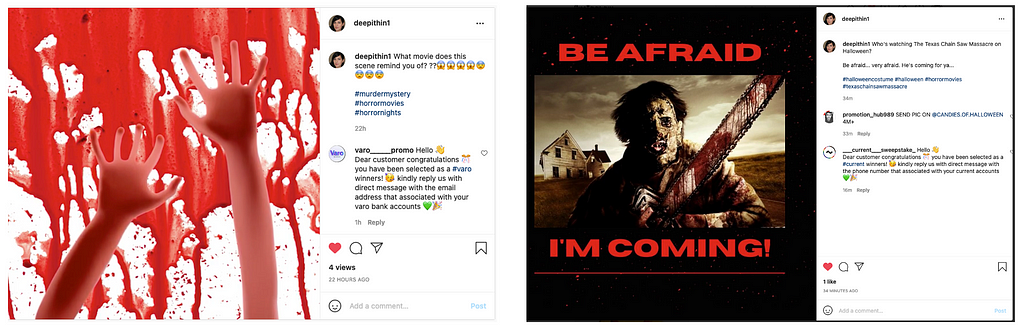
Through the comments attackers are soliciting sensitive information they can use to commit fraud. The comments in Figure 7 ask for the email address and phone number associated with the user’s bank account. The intention of the comments is similar to that of the direct messages discussed earlier. The difference is in the method used by attackers to target the user.
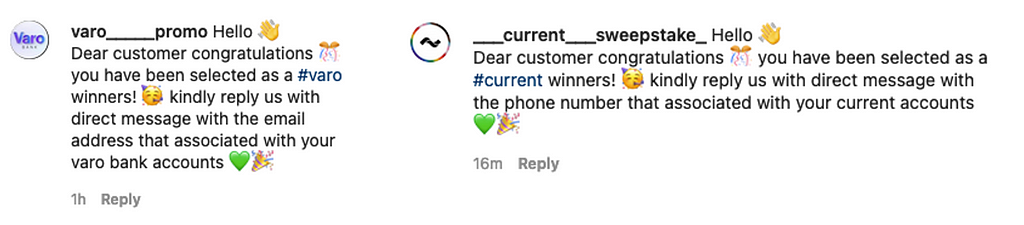
Method 3: Following user’s account
Impersonation accounts created by attackers start following user accounts that follow a brand’s real account. Attackers want to trick users into following the impersonation accounts because users are more likely to fall for scams when they receive messages or comments from accounts they follow. Furthermore, when a user follows an account, that account can send more than one message to the user. Otherwise, it can send only one message, which the user has to approve, before it can send more messages. The ability to send multiple messages aids the attacker in committing fraud more effectively. Figure 8 shows accounts impersonating Current, Chime, Zelle and Yotta following a user’s account.
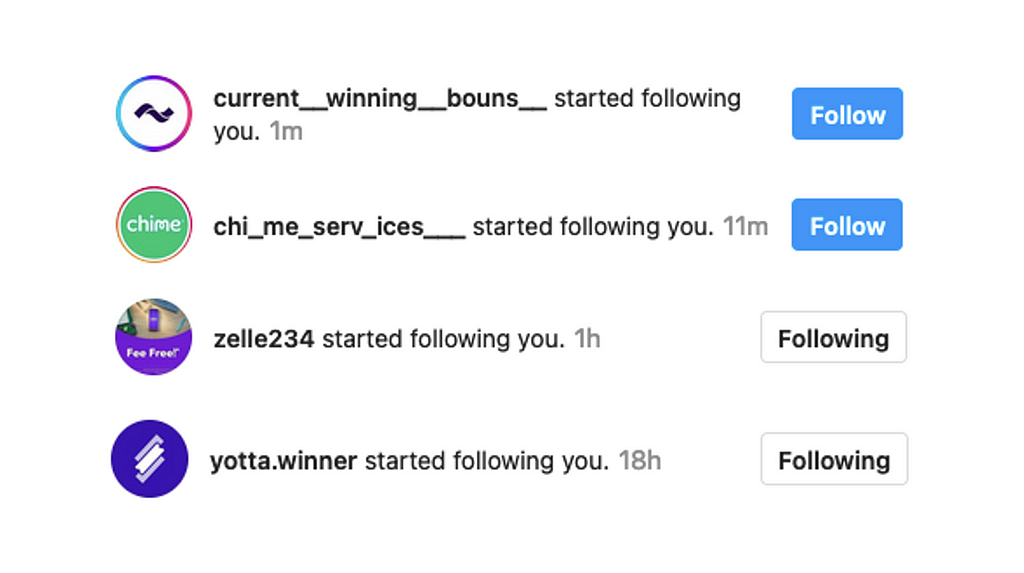
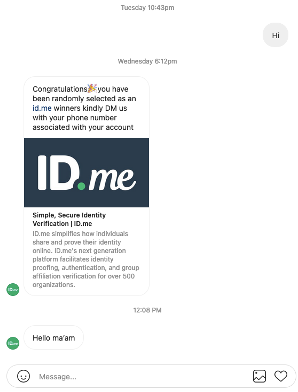
Figure 9 shows a scenario where a user was tricked into following an impersonation account for ID.me, and the user started messaging that account. In response to the message (“Hi”) sent by the user, the attacker requested the phone number associated with user’s ID.me account. If the user thinks that they are interacting with the real brand’s customer service agent or employee, the user is likely to provide sensitive credentials and financial information requested by the attacker.
ID.me is a company that provides identity proofing, authentication and verification services to organizations including the California Department of Motor Vehicles (DMV). If scammers get the ID.me credential of a user, they can use those credentials with any organization or service that uses ID.me to verify the identity of that user.
Impact on brands
The cost of brand impersonation is often felt differently across different functional divisions of a company.
Millions of dollars are spent to create, build and maintain a company’s online brand presence. For many organizations and their customers, the brand is the most valuable asset whose reputation must be protected. Persistent and recurrent phishing and impersonation campaigns not only create a chilling effect on a brand’s customers, they also lead to brand dilution. Customers feel less inclined to engage with such brands and are likely to switch to a competitor’s brand where customers experience fewer phishing attacks.
The rapid increase in impersonation attacks implies an increasing burden of ensuring a secure online presence of the brand by identifying potential attack vectors, mapping and minimizing the attack surface, reducing the likelihood of an attack, and lowering the data loss and damage resulting from an attack. The cost of hiring, training and maintaining staff to address the growing attacks can be significant for any brand in today’s market.
Brand Protection on Social Media
Billions of dollars are lost annually in Internet fraud including impersonation and phishing. It is important to realize that social media accounts are fast becoming alternative inboxes for its users, e.g. DM on Instagram and LinkedIn act as alternative to traditional email inboxes. However, protection against emerging social media attacks has not received the same attention as protection against email phishing attacks.
At Eydle, we specialize in detecting and taking down social media phishing accounts using AI and deep learning tools, which capitalize on our insights that we shared above. Contact us at [email protected] for securing your social media presence and protecting your brand against impersonation scams.
In our next article, which will be Part 3 in this series of blog articles, we will discuss how social media AI algorithms can often recommend users to follow impersonation accounts.
How Attackers Target Brand Followers on Instagram was originally published in Eydle on Medium, where people are continuing the conversation by highlighting and responding to this story.