Previously, we discussed how pig butchering scams hide within mobile app stores as well as impersonate major brands. In this article, we discuss the pig butchering scams that exhibit dual behavior – malicious and benign – by exploiting user’s geolocation.
Like the case of Dr. Jekyll and Mr. Hyde, the pig butchering mobile app displays good behavior when visited from one geolocation (e.g., United States) and scam behavior when visited from another geolocation (e.g., Singapore). This makes it harder to detect the pig butchering scam apps.
To recall, a pig butchering scam is a type of financial scam where the victim is gradually “fattened up” (like a pig) with promises of high returns on investments, only for the scammer to “slaughter” the victim by taking all their money in the end. Generally, these apps allow users to trade in stocks and related assets, with the primary method of payment being crypto and virtual currencies that are hard to trace and recover.
In the last three months, we observed hundreds of such apps listed on Google Play Store and Apple App Store.
Example App
Figure 1 shows an example of a dual behavior app TSNFPRO that was available in Google Play Store. The app has been taken down after it was reported to Play.
Dual Behavior
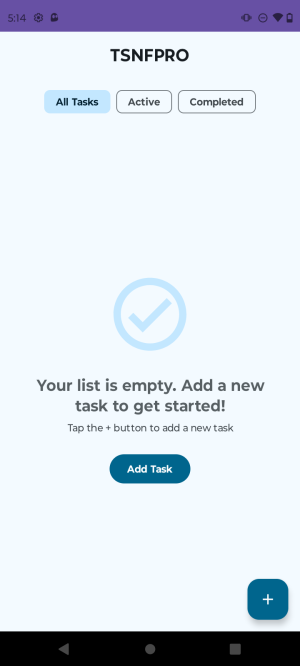
As shown in Figure 2, when accessed from the US geolocation, TSNFPRO app shows a benign behavior, which is task management functionality. A user can add a new task, mark a task as completed and so on. There is no trading-related functionality.
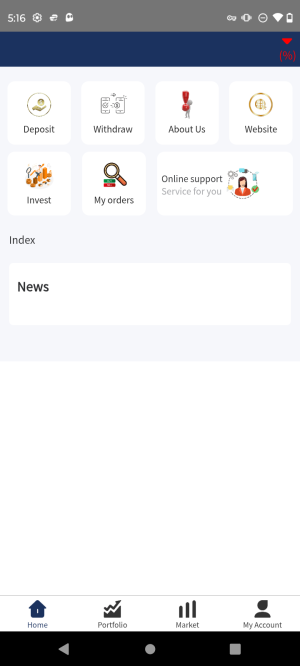
As shown in Figure 3, when accessed from the Singapore geolocation, TSNFPRO shows malicious trading functionality. For example, a user can deposit and withdraw money. They can invest into stocks, check their portfolio, view their orders etc.
The app is using the WebView feature to load the trading functionality from the following phishing website: http://tsnfpro[.]com. Although the TSNFPRO app was taken down from the Play Store, the phishing website is still live as of July 16, 2025.
Technical Details
Android apps can be dangerous when we are unsure if the view we are looking at indeed belongs to the app or a malicious site. WebViews are UI elements allowing developers to embed web content in apps. While this allows developers to reuse existing web content, it introduces the possibility of an app trusting and hosting a malicious html page.
AISLPRO was a dual behavior app similar to TSNFPRO. Both apps used WebViews to display malicious trading functionality. Their benign functionality was implemented natively within their mobile app code.
When we decompile the AISLPRO APK and review its manifest file, we discover the app’s launcher points to a PrivacyActivity. In addition to PrivacyActivity, there is another exported activity called MainActivity.
The PrivacyActivity sets up a WebView with dangerous configurations:
- Access to local files
- JavaScript execution enabled
The PrivacyActivity then loads an external URL https://privacy.lusnakdesign[.]xyz/ Venturepw/AiSLProAsda into a WebView. This website can issue a 302 redirect to https://app.stockoi[.]com based on the user’s geolocation. The redirected website is the AI Stock trading website we mentioned in Figure 2 above. Specifically:
- If the HTTP response returns a 200 status code, a policy page is displayed with an “Accept” button. When the user clicks this button, the app intercepts the event and starts the MainActivity. The MainActivity runs the app code to display the benign task management functionality.
- If the HTTP response returns a 302 status code, the WebView automatically follows the redirect and loads https://app.stockoi[.]com into the WebView. This is the malicious trading functionality.
This design causes the user to unknowingly interact with the trading website through the app’s WebView, while still under the impression they are using the benign app itself.
Effectively, the app is displaying the content of the trading website within a native app screen—without the user’s knowledge or consent. The functionality and branding of the websites have no relation to the apps’ descriptions.
Worse still, because the WebView allows local file access and JavaScript execution, malicious code embedded on that external site could potentially access and exfiltrate local files from the user’s device—putting user privacy and data at risk.
About Eydle
The Eydle Scam Protection platform helps enterprises proactively identify and take down scams that target customers and employees. To learn more, visit our website. For questions regarding the blog post, email [email protected].




