As technology progresses, so do the methods employed by cybercriminals to deceive unsuspecting mobile app users. In this article, we will discuss the latest trends in mobile app scams and provide tips on how to protect yourself from these threats.
The number of apps available on Google Play and the Apple App Store keeps growing each year. In 2022, Google Play reached 3.55 million apps, making it the app store with the largest number of available apps. Meanwhile, the Apple App Store ranked second, with around 1.6 million available apps for iOS [1]. However, the increasing number of apps has also increased mobile fraud. LexisNexis Risk Solutions predicts that losses from mobile fraud will reach $40.3 billion by 2023.
How do fake apps work?
Cybercriminals create fake apps to cause harm to users and their devices. They are designed to look like legitimate apps but perform malicious activities, exploiting user’s familiarity and trust associated with popular applications online. These activities include tracking your movements, installing malware, displaying intrusive advertisements, and stealing your personal information.
Fake apps use a variety of tactics to deceive users and compromise their devices and information. One common method is to distribute apps on third-party or fake app stores, as well as exploit vulnerabilities in official app stores (Google and Apple app stores are examples of official stores). Despite security measures, cybercriminals are able to register as app developers, download legitimate apps, inject them with malicious code, and upload counterfeit versions of a legitimate app. While Google and Apple claim to review apps, fake ones occasionally slip through, especially in third-party stores [2].

Also, scammers use deceptive emails, DMs on social media, or phone SMS messages resembling reputable entities (example: businesses, companies, government agencies, universities) to trick users into downloading malicious apps [4].
The most common types of mobile app fraud categories
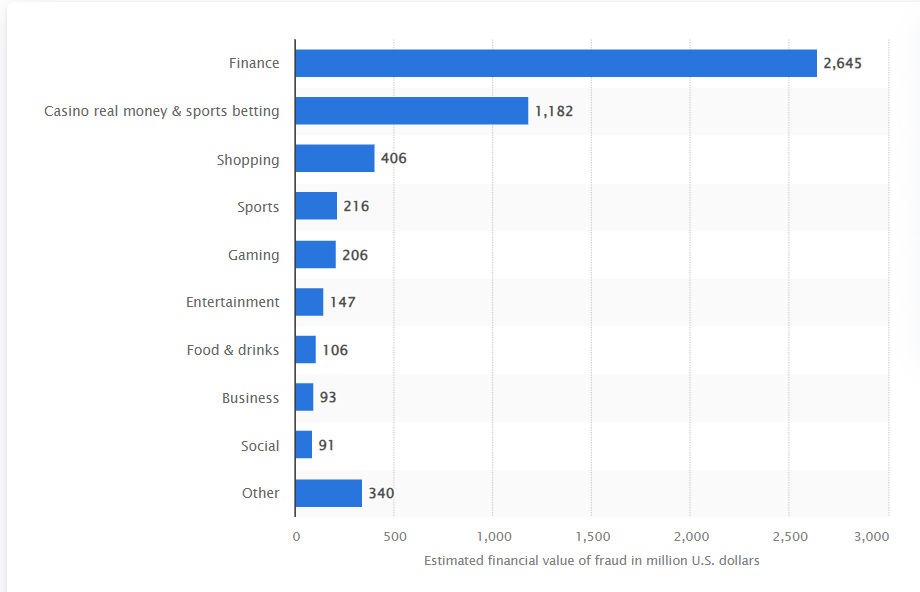
Finance apps have caused the highest amount of losses due to fraud between January 2022 and February 2023, with a global estimated loss of over 2.64 billion U.S. dollars. Other frequently targeted apps are casino and sports betting apps, with an estimated loss of almost 1.2 billion U.S. dollars during the same period. One of the most common types of mobile app fraud is cost-per-install (CPI) fraud, which tricks advertisers into paying a scammer for fraudulent or fake app installs by users. For instance, scammers may create counterfeit versions of well-known apps like ChatGPT, promising free access to premium features while delivering malware instead [5].
Fake apps warning signs
Recognizing the signs of fraudulent applications helps users make informed decisions and protect their digital well-being. Here are key indicators that should not be overlooked [2]:
- Inconsistent app descriptions: Fake apps often have misleading or poorly written descriptions with many grammatical errors, vague information, and low-quality branding images and icons.
- Suspicious app reviews: Authentic reviews are valuable indicators for users. That’s why scammers may create generic or overly positive reviews to boost the app’s credibility.
- Low download numbers: Legitimate apps typically receive a significant number of downloads. If an app has a low download count despite being available for a long time, it may require further investigation.
- Unusual permission requests: Pay attention to the permissions requested during installation. If an app asks for unnecessary access to personal information or features unrelated to its intended purpose, it could be a red flag. Fake apps are often used by cybercriminals to steal contact and credit card information. Recently, Apple had to remove a fraudulent crypto app named “Trezor Wallet Suite” as it was demanding the user’s seed phrases—the codes required to access and recover crypto wallets [6].
- Lack of information: Legitimate apps are associated with verified developers. Make sure to carefully examine the screenshots, dates of releases, and ways to get in touch with the application provider. Also, ensure that the app has a clear description of what it does and that it has an official website or social media presence.
- Unexpected Pop-Ups: Fake apps may redirect users to unfamiliar websites or display intrusive pop-ups. Legitimate apps typically do not engage in such behavior, so encountering these elements is a warning sign.
- In-app advertisements: Authentic apps may contain ads, but excessive or intrusive advertisements within the app could be indicative of a fake application.
- Unusual app file size: Important insights regarding an app’s functionality can be inferred from its file download size. Inadequate size could result from the app missing important features, while excessive size can imply harmful content inside the app. For instance, the most commonly used Android apps have an average size of about 60 MB, while the top iOS apps have an average size of roughly 174 MB [source].
Preventive measures against fake apps
Protect yourself from fraudulent apps while exploring the vast world of applications by following these practical steps [2] [7]:
- It is recommended to only download apps from official app stores like Google Play Store or Apple App Store. These stores have strict security measures in place to prevent the installation of fake apps.
- Examine all the permissions an app requests during installation. Be cautious if an app seeks access to unnecessary data or features unrelated to its intended function.
- Read and verify user reviews and ratings before downloading an app. Authentic reviews from other users can provide insights into the app’s legitimacy and performance.
- Research information about the app developer. Legitimate apps are usually associated with well-known and verified developers or companies.
- Regularly update your apps to ensure you have the latest security features and bug fixes. Developers often release updates to address vulnerabilities and enhance app security.
- Install reputable security software on your device. This adds an extra layer of protection by identifying and blocking potential threats, including fake apps.
- Avoid clicking on links or downloading apps from unsolicited messages sent via social media, email, or SMS. Scammers frequently use phishing messages to trick users into downloading fake apps.
- If an app seems suspicious or behaves unexpectedly, trust your instincts. Uninstall the app and report it if necessary.
Take preventive measures to avoid fake apps and stay safe while using your mobile.
Protect your online presence with Eydle
Secure your digital footprint and elevate your online security with Eydle. At Eydle, we offer cutting-edge online security services that go beyond traditional security measures. Our team of cybersecurity experts and AI leaders from renowned institutions such as MIT, Stanford, and Carnegie Mellon has developed advanced technologies to safeguard your business from online threats.
Eydle’s monitoring solutions keep your online presence one step ahead of impersonation attempts by fake accounts. Do not wait for potential fraud to strike; fortify your defenses now!
Discover more about our protective measures by visiting www.eydle.com or reaching out to us at [email protected].
Resources:
[1] https://www.statista.com/statistics/276623/number-of-apps-available-in-leading-app-stores/
[2] https://www.aura.com/learn/how-to-spot-fake-apps
[3] https://www.sydney.edu.au/news-opinion/news/2019/06/24/over-2-000-fake-android-apps-discovered.html
[4] https://www.avast.com/c-phishing
[5] https://www.statista.com/statistics/1380417/app-fraud-value-by-category/
[6] https://cointelegraph.com/news/fake-trezor-crypto-app-removed
[7] https://www.kaspersky.com/resource-center/preemptive-safety/identifying-and-avoiding-fake-apps
Unmasking Fake Apps: Secure Your Device and Data was originally published in Eydle on Medium, where people are continuing the conversation by highlighting and responding to this story.